Understanding What is a DDoS Attack & Prevention

Welcome to our article where we will provide you with a comprehensive understanding of what a DDoS attack is and discuss effective prevention strategies. So, what exactly is a DDoS attack?
A DDoS attack, short for Distributed Denial of Service attack, is a malicious attempt to disrupt the regular functioning of a network, website, or service by overwhelming it with a flood of internet traffic. These attacks aim to render the targeted online assets inaccessible to legitimate users, causing inconvenience, financial loss, and even reputational damage.
Now that we have defined a DDoS attack, let’s dive deeper into its various aspects and explore how you can protect your online assets from such threats.
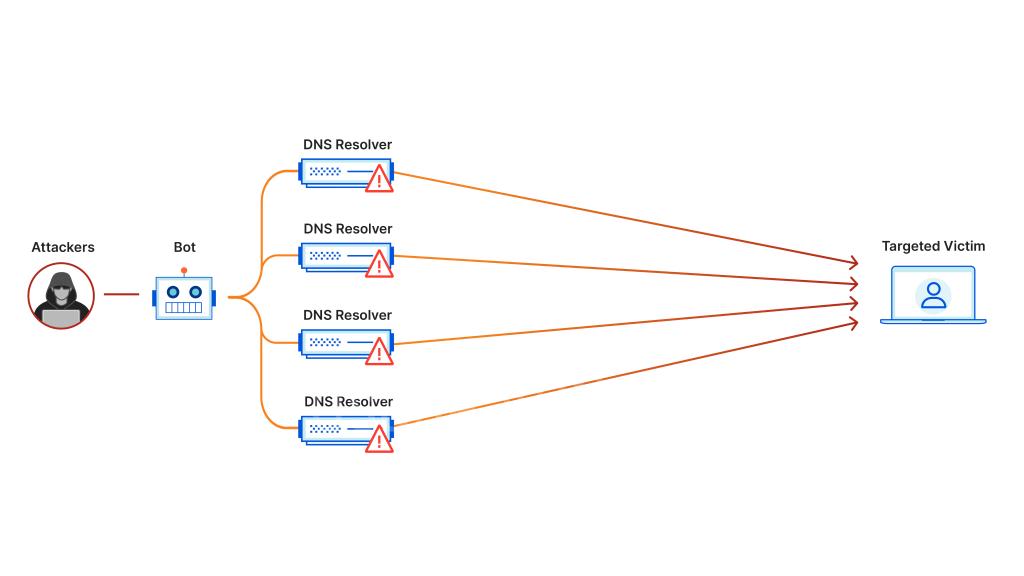
Types of DDoS Attacks
In this section, we will explore the various types of DDoS attacks that cybercriminals employ to disrupt online services. By understanding the characteristics and techniques used in each attack, you will gain a deeper insight into the diverse ways DDoS attacks can be executed.
1. Volume-Based Attacks
- SYN Flood
- UDP Flood
- ICMP Flood
2. Protocol Attacks
- HTTP Flood
- Slowloris
- Smurf Attack
3. Application Layer Attacks
- HTTP GET/POST Flood
- SIP Invite Flood
- DNS Amplification
4. Fragmentation Attacks
- IP Fragmentation
- TCP Fragmentation
Each attack type has its unique characteristics and requires specific defense mechanisms for effective protection. By familiarizing yourself with these various types of DDoS attacks, you can better prepare yourself to mitigate their impact and safeguard your online presence.
Implementing Robust DDoS Prevention Strategies
When it comes to protecting your online assets from DDoS attacks, proactive prevention strategies play a crucial role. By implementing the right measures, such as ddos prevention, ddos mitigation, and ddos protection, you can safeguard your network and mitigate the impact of potential attacks.
One approach to bolstering your defenses is to focus on network-level protections. This involves implementing firewalls, load balancers, and intrusion detection systems to monitor and filter incoming traffic. Such measures can help identify and block malicious traffic, preventing it from overwhelming your network and causing disruption.
In addition to network-level defenses, it’s essential to consider specialized DDoS mitigation services. These services are designed to detect and mitigate DDoS attacks in real-time, ensuring the continuity of your online services. By leveraging the expertise and resources of these dedicated providers, you can quickly identify and divert malicious traffic away from your network, minimizing the impact of an attack.
Furthermore, a robust prevention strategy includes proactive monitoring and analysis of network traffic patterns. By continuously monitoring your network, you can identify anomalies and potential signs of a DDoS attack before it escalates. This allows you to take prompt action and implement countermeasures to mitigate the impact effectively.
In summary, implementing robust DDoS prevention strategies is essential to protect your online assets. By combining network-level defenses, specialized DDoS mitigation services, and proactive monitoring, you can fortify your network and ensure the uninterrupted availability of your online services.
Key Points:
- Network-level defenses such as firewalls and intrusion detection systems are crucial for ddos prevention.
- Specialized DDoS mitigation services can quickly detect and divert malicious traffic away from your network.
- Proactive monitoring and analysis of network traffic patterns help identify potential signs of a DDoS attack.
Examples of DDoS Attacks
In this section, we will explore real-world examples of notable DDoS attacks that have occurred in the past. By examining these case studies, we can gain valuable insights into the destructive potential of DDoS attacks and learn from the experiences of others.
1. Mirai Botnet Attack:
One of the most infamous DDoS attacks in recent history, the Mirai botnet attack, took place in 2016. This attack utilized a massive botnet consisting of compromised IoT devices to generate an unprecedented amount of traffic. By targeting DNS provider Dyn, the attack disrupted internet access for major websites such as Twitter, Netflix, and The New York Times. This attack served as a wake-up call to the vulnerabilities of IoT devices and highlighted the need for stronger cybersecurity measures.
2. GitHub’s 1.35 Tbps Attack:
In 2018, GitHub was targeted by a massive DDoS attack that reached a peak traffic volume of 1.35 terabits per second (Tbps), making it one of the largest attacks ever recorded. The attack used the amplification technique of exploiting vulnerable UDP-based protocols. Despite the scale of the attack, GitHub was able to mitigate the impact and maintain its services thanks to its robust DDoS protection infrastructure and incident response strategies.
3. Dyn DNS Attack:
In 2016, Dyn, one of the largest DNS providers, was hit by a series of DDoS attacks that disrupted access to major websites and services, including Twitter, Amazon, and Spotify. The attack leveraged a botnet consisting of compromised IoT devices infected with the Mirai malware. This attack highlighted the potential impact of targeting critical infrastructure such as DNS providers, underscoring the importance of implementing resilient defenses and multi-layered security measures.
4. ProtonMail Attack:
ProtonMail, a secure email provider, fell victim to a powerful DDoS attack in 2015. The attack aimed to disrupt the service and extort the company for a ransom payment. ProtonMail successfully defended against the attack by leveraging its DDoS protection measures and collaborating with the cybersecurity community. This incident demonstrated the necessity of proactive defenses and the benefits of open collaboration in combating DDoS attacks.
5. PlayStation Network Christmas Attack:
In 2014, the PlayStation Network (PSN) experienced a series of DDoS attacks during the holiday season, leaving millions of gamers unable to access the online platform. The attacks targeted the PSN servers and overwhelmed them, causing service disruptions. This high-profile attack highlighted the impact that DDoS attacks can have on online gaming services and emphasized the importance of robust security measures for gaming networks.
By examining these notable DDoS attack examples, we can gain a better understanding of the techniques and impact of such cyber threats. Such insights can help organizations develop effective DDoS prevention and mitigation strategies to safeguard their online assets.
Conclusion
DDoS attacks pose a significant threat to online businesses and organizations. Throughout this article, we have explored the ins and outs of DDoS attacks, gaining a comprehensive understanding of their definition, various types, prevention strategies, and real-world examples.
It is crucial to recognize the importance of being well-informed about DDoS attacks and implementing effective prevention measures. By staying one step ahead of potential attackers, you can safeguard your online presence, protect your valuable data, and ensure uninterrupted service for your customers.
With the ever-evolving nature of cyber threats, it is recommended to regularly update your prevention strategies and stay updated on the latest attack trends. Utilizing a combination of network-level defenses, specialized DDoS mitigation services, and proactive monitoring, you can significantly reduce the risk of falling victim to a DDoS attack.
Remember, prevention is key. By investing time and resources into understanding DDoS attacks and implementing robust prevention strategies, you can fortify your online infrastructure and mitigate the potential damage caused by these disruptive cyber threats.
FAQ
What is a DDoS attack?
A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt the normal functioning of a network, service, or website by overwhelming it with a flood of internet traffic. The goal of a DDoS attack is to render the targeted system inaccessible to its intended users.
Can you provide a definition of a DDoS attack?
A DDoS attack can be defined as a coordinated and simultaneous assault on a target by a large number of compromised computers or devices, known as a botnet. The massive influx of traffic generated by the botnet overwhelms the target, causing it to slow down or crash altogether.
What are the types of DDoS attacks?
There are several types of DDoS attacks, including volumetric attacks, which flood the target with a high volume of traffic; protocol attacks, which exploit vulnerabilities in network protocols; and application layer attacks, which target web applications and services. Other types include ICMP and DNS attacks.
How can I prevent DDoS attacks?
Preventing DDoS attacks involves implementing robust cybersecurity measures. This can include network-level defenses such as firewalls and intrusion detection systems, as well as utilizing specialized DDoS mitigation services that can identify and block malicious traffic. Regularly updating and patching software can also help prevent vulnerabilities that attackers may exploit.
What are some examples of DDoS attacks?
Some notable examples of DDoS attacks include the 2016 Dyn attack, which targeted major websites and services, causing widespread outages; the 2020 Amazon Web Services attack, which disrupted various online services; and the 2021 GitHub attack, which disrupted developers’ access to the popular coding platform. These attacks highlight the disruptive potential of DDoS attacks.
