How Does a VPN Tunnel Work? A Beginner’s Simple Guide
In today's digital world, nearly every aspect of our lives is connected to the internet. From banking and shopping to communicating with loved ones, we send a constant stream of personal data across public networks. This convenience, however, comes with a significant risk to our privacy and security. Anyone from your Internet Service Provider (ISP) to malicious actors on a public Wi-Fi network could potentially intercept and view your online activities. This is where a Virtual Private Network (VPN) becomes an essential tool for digital self-defense. At the heart of this technology is a powerful mechanism that shields your data from prying eyes. If you've ever wondered what is a vpn tunnel and how it magically protects your information, you've come to the right place. This guide will demystify the process, breaking down how a VPN tunnel works in simple, easy-to-understand terms.
How Does a VPN Tunnel Work? A Beginner's Simple Guide
The Core Concept: What is a VPN Tunnel?
Imagine the internet as a vast, public highway system. Every time you visit a website, send an email, or stream a video, your data travels on this highway in a standard vehicle (a data packet). Anyone with the right tools positioned along the highway—like your ISP, government agencies, or hackers—can look inside your vehicle and see exactly what you're carrying and where you're going. This lack of privacy is the default state of most internet connections. Your data is exposed, labeled with your IP address (your digital home address), and vulnerable to interception.
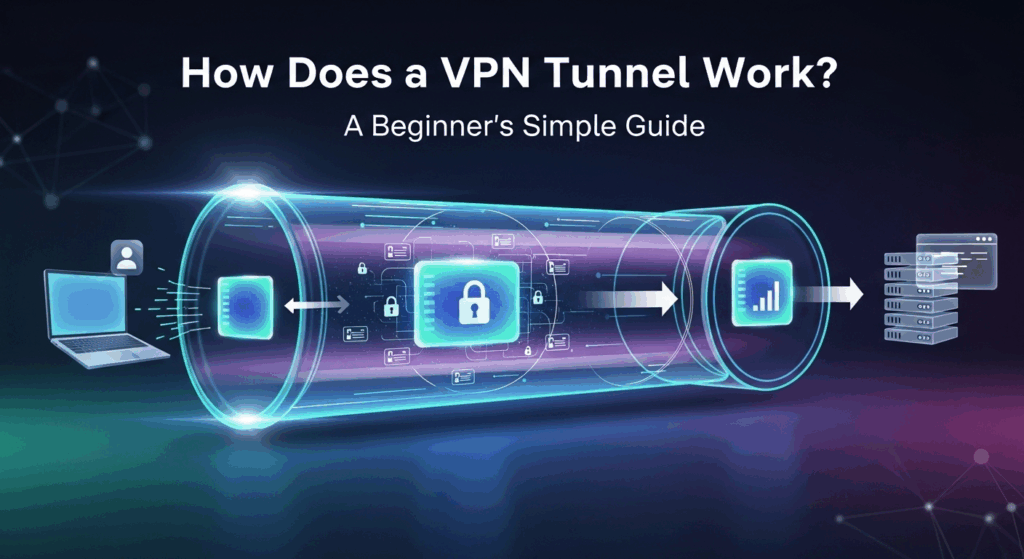
A VPN tunnel fundamentally changes this dynamic. Think of it as creating a private, opaque, and armored tunnel that runs directly through the public highway system. When you connect to a VPN, your data is no longer sent in a standard, transparent vehicle. Instead, it's placed inside a heavily armored transport vehicle before it even leaves your device. This vehicle then enters the private tunnel, which leads directly from your device to a secure VPN server. From the outside, no one can see what's inside the armored vehicle, who sent it, or its final destination beyond the VPN server's exit point.
This process of enclosing your data within a secure passage is the essence of VPN tunneling. The "tunnel" is not a physical structure but a virtual connection built with layers of security protocols and encryption. It effectively creates a private network for you over the public internet infrastructure. Once your data reaches the VPN server at the other end of the tunnel, it is un-packaged and sent on to its final destination (e.g., the website you want to visit). The website sees the request as coming from the VPN server, not your personal device, which effectively masks your real IP address and location, adding another crucial layer of privacy.
The Step-by-Step Process of VPN Tunneling
Creating this secure tunnel isn't instantaneous magic; it's a carefully orchestrated, multi-step process that happens in milliseconds. It involves your device (the VPN client), the VPN server, and a set of rules known as a tunneling protocol. The primary goal is to establish a trusted, encrypted link before any of your actual internet traffic is sent. This ensures that from the very first bit of data, your connection is shielded from a public view.
The journey begins the moment you click "Connect" on your VPN application. Your device sends out an initial communication request to the VPN server you've selected. This first handshake is critical. Your device and the server need to agree on the security parameters they will use to build the tunnel, including the protocol and the encryption keys they will share. This is like two security agents agreeing on a secret code and a secure route before beginning a mission.
Once the secure parameters are agreed upon and both parties have verified each other's authenticity, the tunnel is officially established. From this point on, all your designated internet traffic is automatically rerouted. Instead of going directly from your device to your ISP and then to the open internet, it first travels through this encrypted tunnel to the VPN server. The server then acts as your intermediary, forwarding your requests to the internet on your behalf and sending the responses back to you through the same secure tunnel.
Authentication: The Entry Gate
Before any data can be protected, the tunnel's security must be established. The first step is authentication, which is essentially the process of your device proving its identity to the VPN server and vice-versa. This is the security checkpoint at the entrance of the tunnel, ensuring that only authorized users are allowed in. Without this step, anyone could potentially connect to the VPN server and compromise its integrity, defeating the purpose of the network.
This verification can happen in several ways. The most common method for personal VPN services involves a username and password. When you log in to your VPN app, your credentials are securely sent to the server for verification. In corporate environments, authentication is often more robust, using digital certificates. A certificate is a unique cryptographic file installed on an employee's device, which acts as a non-forgeable ID card. The VPN server checks this certificate to confirm the device is authorized to access the company's private network. This two-way trust is vital for creating a truly secure connection.
Encapsulation: Creating the Secure Packet
Once authentication is complete, the process of encapsulation begins. This is where your data is packaged for its journey through the tunnel. Imagine your original data packet is a postcard with a message and your address written on it for everyone to see. Encapsulation is the process of taking that postcard and sealing it inside a thick, tamper-proof security envelope. This "envelope" is a new, outer data packet created by the VPN.
The original data packet, containing your actual request (e.g., to load google.com), is placed—unaltered—inside the payload of this new packet. The outer packet is then given a new header with routing information. However, instead of being addressed to the final destination (google.com), it's addressed to the VPN server. This process, also known as IP-in-IP encapsulation, effectively hides the true destination and content of your traffic from your ISP or anyone else snooping on the local network. They can only see that you've sent an encapsulated packet to a VPN server's IP address.
Encryption: Scrambling the Message
Encapsulation hides the destination, but encryption protects the content. If encapsulation is putting the postcard in an envelope, encryption is writing the original message in an unbreakable code before you even put it in the envelope. Even if a highly sophisticated attacker managed to intercept your traffic and "open" the outer packet, they would still be left with a jumbled, unreadable mess of data. This scrambling of data is a cornerstone of VPN security.
VPNs use powerful encryption algorithms (ciphers) and an encryption key to transform your readable data (plaintext) into an unreadable format (ciphertext). The most secure VPNs today use AES (Advanced Encryption Standard) with 256-bit keys, the same encryption standard trusted by governments and security agencies worldwide. To decrypt the data, one would need the corresponding key, which is securely shared between your device and the VPN server during the initial handshake. Without this key, trying to break AES-256 encryption would take the world's most powerful supercomputers billions of years, making it practically impossible.
Understanding VPN Tunneling Protocols
The "blueprints" used to build a VPN tunnel are known as tunneling protocols. These protocols are sets of rules and procedures that determine how authentication, encapsulation, and encryption are handled. Different protocols offer varying balances of speed, security, and stability. Think of them as different construction methods for building your secure tunnel; some are faster and lighter, while others are slower but more heavily fortified.
Choosing the right protocol can impact your VPN experience. For instance, a protocol designed for maximum security might introduce a slight speed reduction due to its complex encryption processes, making it ideal for handling sensitive data. On the other hand, a protocol optimized for speed might be better for streaming or gaming, where low latency is crucial. A good VPN provider will offer a selection of top-tier protocols, allowing users to choose the best one for their needs or, more commonly, automatically selecting the optimal protocol based on the network conditions.
Most modern VPN applications handle this complexity for you, but understanding the key players is valuable. Protocols like OpenVPN are known as the industry standard for their excellent balance of robust security and good performance. WireGuard® is a newer, more modern protocol renowned for its incredibly fast speeds and streamlined, state-of-the-art cryptography. IKEv2/IPsec is another popular choice, especially favored on mobile devices for its stability and ability to quickly reconnect if the connection drops. The table below provides a simple comparison of these common protocols.
| Protocol | Typical Speed | Security Strength | Best For |
|---|---|---|---|
| OpenVPN | Good to Very Good | Very High (Highly configurable) | All-purpose use, security-critical tasks, bypassing firewalls. |
| WireGuard® | Excellent | Very High (Modern cryptography) | Streaming, gaming, and general use where speed is a priority. |
| IKEv2/IPsec | Very Good | High | Mobile devices, users who frequently switch between Wi-Fi and mobile data. |
| L2TP/IPsec | Fair | Moderate (Slower, can be blocked) | Non-critical tasks; now largely superseded by better options. |
The Real-World Benefits of Using a VPN Tunnel
Understanding the technical mechanics of a VPN tunnel is one thing, but its true value lies in how it translates to real-world benefits for the average internet user. The primary function of this secure tunnel is to reclaim your digital privacy and fortify your online security. In an era of rampant data collection and cyber threats, a VPN acts as your personal digital bodyguard.
The most immediate benefit is enhanced privacy from your ISP. Without a VPN, your ISP can see every website you visit, how long you spend there, what you download, and more. They often collect and monetize this data by selling it to advertisers. When you use a VPN tunnel, all your ISP can see is encrypted traffic flowing to a single VPN server. Your browsing history, search queries, and communications become completely opaque to them, putting you back in control of your personal information.
Furthermore, a VPN is an indispensable tool for securing your data on public Wi-fi networks. When you connect to the internet at a coffee shop, airport, or hotel, you are on a shared, often unsecured network. This makes you an easy target for hackers using "man-in-the-middle" attacks to steal your passwords, credit card details, and other sensitive information. A VPN tunnel encrypts all your data before it leaves your device, making it unreadable to anyone else on the same network. Even if a hacker intercepts your data, they'll only see scrambled gibberish.

Bypassing Geoblocking and Censorship
One of the most popular uses for a VPN tunnel is to circumvent geographic restrictions, also known as geoblocking. Many streaming services, news websites, and online platforms restrict their content to specific countries due to licensing agreements. A VPN tunnel allows you to connect to a server in a different country. When you do this, your internet traffic exits the tunnel from that server, adopting its IP address.
For example, if you are in France and want to watch a show that is only available on a U.S. streaming platform, you can connect to a VPN server located in New York. The streaming service will see your connection originating from New York and grant you access to its U.S. library. This same principle applies to overcoming internet censorship in countries where governments block access to certain social media platforms, news sites, or communication apps. A VPN tunnel provides a secure and private pathway to the open internet.
Securing Remote Work
In the age of remote and hybrid work, VPN tunnels have become a cornerstone of corporate cybersecurity. Companies need to ensure that when employees access sensitive company files, internal applications, and private databases from their home networks, the connection is completely secure. A corporate VPN creates an encrypted tunnel directly from the employee's computer to the company's internal network.
This ensures that confidential company data is protected from interception as it travels over the public internet. It prevents unauthorized access and maintains the integrity of the corporate network, just as if the employee were physically present in the office. This secure access is critical for protecting trade secrets, customer data, and financial information, making VPNs an essential technology for modern businesses.
Advanced Concepts: What is Split Tunneling?
While routing all your traffic through a VPN tunnel provides maximum security, it's not always the most practical solution. Sometimes, you may want to access local network devices (like a wireless printer) or need the fastest possible connection for a latency-sensitive application like online gaming. This is where an advanced feature called split tunneling comes in. It allows you to choose which apps or websites use the VPN tunnel and which connect directly to the internet.
Split tunneling offers a flexible, best-of-both-worlds approach. You can configure it to route only specific traffic through the VPN, while the rest of your traffic bypasses it. For example, you could secure your browsing and torrenting traffic through the VPN tunnel while allowing your Netflix app to connect directly to the internet to ensure you can access your local content library and get the best streaming speed. This feature gives you granular control over your connection.
There are several practical use cases where split tunneling is incredibly useful:
- Securing work traffic while streaming music or video from a local service that might be blocked by your company's VPN.
- Downloading files securely through the VPN while playing online games on a low-latency, direct connection.
- Accessing local network devices, such as printers or file servers, without having to disconnect from the VPN.
This feature adds a layer of convenience and efficiency, allowing you to tailor your VPN usage to your specific, moment-to-moment needs without compromising on the security of the data that matters most.
Frequently Asked Questions about VPN Tunnels
Q: Is a VPN tunnel completely foolproof and 100% secure?
A: While a VPN tunnel provides incredibly strong security for your data in transit, it's not a magic bullet that protects against all online threats. It encrypts your connection, but it cannot protect you from malware or viruses if you download a malicious file, nor can it stop you from falling for a phishing scam where you voluntarily give away your information. It's best used as part of a comprehensive security strategy that also includes antivirus software and practicing safe browsing habits.
Q: Does a VPN tunnel make me completely anonymous online?
A: A VPN significantly enhances your privacy, but it does not necessarily grant you complete anonymity. It hides your IP address and encrypts your traffic from your ISP and third parties, but the VPN provider itself can, in theory, see your activity. This is why it is absolutely critical to choose a reputable VPN provider with a strict, independently audited no-logs policy. This policy guarantees that the provider does not store any records of your online activities, so even if they were compelled to share data, there would be nothing to share.
Q: Will using a VPN tunnel slow down my internet connection?
A: Yes, using a VPN will almost always introduce some reduction in speed. This is because of the extra steps involved: encrypting and decrypting data and routing it through an additional server. However, with premium VPN providers and modern protocols like WireGuard®, this speed loss is often negligible and unnoticeable for most activities. The extent of the slowdown depends on several factors, including the encryption strength, the distance to the VPN server, and the current load on that server.
Q: Can my ISP see that I am using a VPN?
A: Yes, your ISP can detect that you are connected to a VPN. They can see that encrypted data packets are traveling between your device and the IP address of a VPN server. However, thanks to the encryption within the VPN tunnel, they cannot see the content of that data. They won't know which websites you are visiting, what you are downloading, or who you are communicating with. All they see is a secure, private tunnel, and they cannot look inside.
Conclusion: Your Gateway to a Safer Internet
Understanding how a VPN tunnel works empowers you to take meaningful control of your digital life. It’s not just a tool for tech experts; it's a practical and accessible solution for anyone who values their privacy and security online. By creating an encrypted, private pathway for your data through the public internet, a VPN tunnel shields your activities from ISPs, secures your information on public Wi-Fi, and unlocks a more open and unrestricted internet experience.
From the initial handshake and authentication to the powerful combination of encapsulation and military-grade encryption, every step of the tunneling process is designed with one goal: to protect your data. Now that you've demystified the technology, you can confidently use a VPN not as a complex piece of software, but as your personal key to a safer, more private, and more free online world.
***
Summary
This article, "How Does a VPN Tunnel Work? A Beginner's Simple Guide," provides a comprehensive yet accessible explanation of VPN tunneling technology for a non-technical audience. It begins by introducing the core concept using the analogy of a private, armored tunnel on the public internet highway, contrasting it with the exposure of a standard connection.
The article then breaks down the step-by-step process of how a VPN tunnel is created, detailing three critical stages: Authentication (verifying identity), Encapsulation (packaging data into a secure outer packet), and Encryption (scrambling the data's content with algorithms like AES-256).
It further explores the different VPN protocols (like OpenVPN and WireGuard®) that act as the blueprints for these tunnels, presenting their pros and cons in a comparison table. The guide connects these technical details to tangible, real-world benefits such as enhancing privacy from ISPs, securing data on public Wi-Fi, bypassing geo-restrictions, and enabling secure remote work. An advanced feature, split tunneling, is also explained as a flexible way to route only specific traffic through the VPN. The article concludes with a helpful FAQ section addressing common user questions about security limitations, anonymity, and potential speed loss, solidifying the reader's understanding and empowering them to use VPNs effectively.
