Different Types Of VPN? When to Use Them?

Welcome to our comprehensive guide on different types of VPN, VPN services, and secure VPN connections. In this article, we will explore the various options available to help you determine the right VPN for your specific needs. Whether you’re looking for personal use or business purposes, our aim is to provide you with the information needed to make an informed decision.
VPN services play a crucial role in safeguarding your online activities, protecting your sensitive data, and enhancing your privacy. With the ever-increasing threats in the digital landscape, it is essential to understand the different types of VPNs and when to use them to ensure a secure online experience.
So, let’s dive into the world of VPNs and discover how they can enhance your online security and anonymity. Whether you’re a streamer, a privacy-conscious user, or someone who frequently connects to public Wi-Fi networks, there’s a VPN solution tailored to your requirements. Let’s get started!
What is a VPN and How Does it Work?
A Virtual Private Network (VPN) is a technology that enables secure and private communication over public networks. It allows users to establish a secure connection to a remote server, encrypting their internet traffic and ensuring their online activities remain private and protected.
When you connect to a VPN, your device creates a secure tunnel between your device and the VPN server. All your internet traffic is routed through this tunnel, protecting it from potential eavesdropping or interception by hackers or government surveillance. This effectively masks your IP address and location, making it difficult for anyone to track your online activities.
VPNs rely on various protocols to establish secure connections between devices and servers. These protocols define how data is transmitted and encrypted to ensure secure communication. Common VPN protocols include:
- OpenVPN: OpenVPN is an open-source protocol that provides strong security and is widely regarded as one of the most secure VPN protocols available. It uses OpenSSL encryption and can operate on both TCP and UDP ports.
- IPSec: Internet Protocol Security (IPSec) is a suite of protocols used to secure internet communication. It provides secure authentication and encryption and can be used for remote access VPNs or site-to-site VPNs.
- L2TP/IPSec: Layer 2 Tunneling Protocol (L2TP) combined with IPSec provides an additional layer of security. L2TP establishes the tunnel while IPSec ensures the confidentiality and integrity of the data.
- PPTP: Point-to-Point Tunneling Protocol (PPTP) is one of the oldest VPN protocols. While it offers faster connection speeds, it is considered less secure than other protocols due to potential vulnerabilities.
Comparison of VPN Protocols
| Protocol | Security | Speed | Platform Compatibility |
|---|---|---|---|
| OpenVPN | High | Medium | Windows, Mac, Linux, Android, iOS |
| IPSec | High | Medium | Windows, Mac, Linux, Android, iOS |
| L2TP/IPSec | Medium | Medium | Windows, Mac, Linux, Android, iOS |
| PPTP | Low | High | Windows, Mac, Linux, Android, iOS |
Choosing the appropriate VPN protocol depends on your security, speed, and platform compatibility requirements. OpenVPN and IPSec are commonly recommended for their high levels of security, while PPTP may be suitable for users prioritizing speed.
In conclusion, a VPN is a powerful tool that enhances security and privacy by encrypting your internet traffic and creating a secure connection to a remote server. Various VPN protocols provide different levels of security, giving users the flexibility to choose the protocol that best suits their needs.
Types of VPNs for Personal Use
When it comes to personal use, there are several popular VPN options available in the market. These VPN services offer various features and functionalities to cater to your specific needs. In this section, we will compare some of the top VPN services and help you make an informed decision.
Comparison of Popular VPN Services
Let’s take a look at the key features and benefits of some of the leading VPN providers:
| VPN Provider | Features | Benefits |
|---|---|---|
| ExpressVPN |
|
|
| NordVPN |
|
|
| CyberGhost |
|
|
With this comparison, you can assess the features and benefits of each VPN provider and choose the one that aligns best with your personal requirements. Remember to consider factors like speed, security, server locations, and device compatibility when making your decision.
Types of VPNs for Business Use
Business organizations have specific VPN requirements to ensure secure connections and protect sensitive data. Let’s explore the types of VPNs suitable for business use, as well as the importance of secure VPN connections and the role of VPN client software.
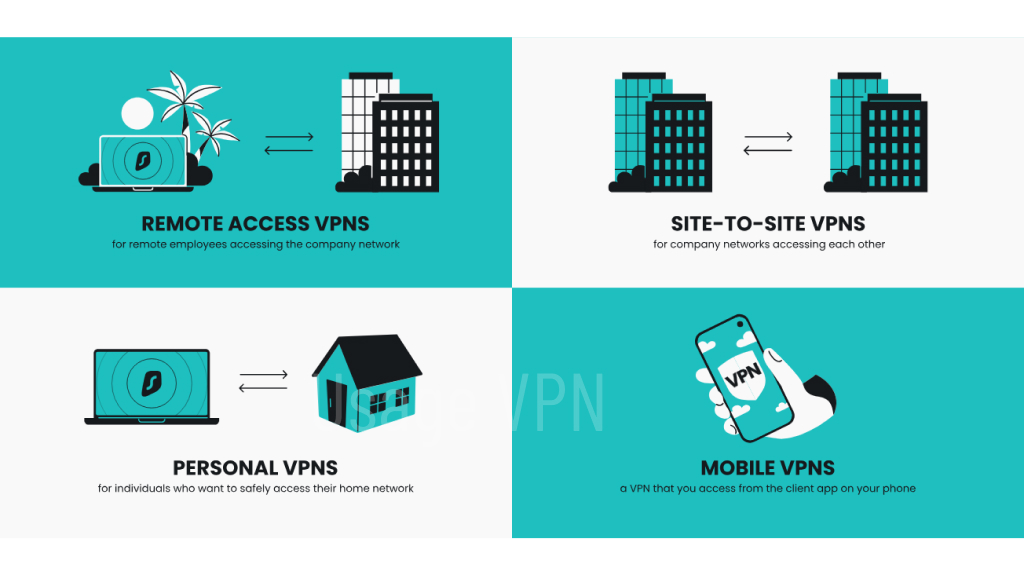
1. Site-to-Site VPN
A site-to-site VPN allows multiple offices or branches of an organization to connect securely over the internet. It establishes a virtual network between the different locations, creating a private and encrypted connection. This type of VPN is ideal for businesses with multiple offices that need to communicate and share resources securely.
2. Remote Access VPN
A remote access VPN enables employees to securely connect to their organization’s network from remote locations. It allows individuals to access company resources such as files, applications, and databases as if they were directly connected to the office network. Remote access VPNs are essential for businesses with employees working from home or on the go.
3. Extranet VPN
An extranet VPN extends the secure network connection beyond the organization’s boundaries to trusted external entities such as suppliers, partners, or clients. It enables secure collaboration and data sharing between the organization and external stakeholders. Extranet VPNs are crucial for businesses that require secure communication and information exchange with third parties.
4. MPLS VPN
Multi-Protocol Label Switching (MPLS) VPN is a type of VPN that utilizes MPLS technology to provide secure and reliable communication between different locations. It establishes virtual private networks within a service provider’s network infrastructure, allowing businesses to connect their offices worldwide securely. MPLS VPNs are ideal for enterprises with a global presence and need consistent, high-performance connectivity.
| VPN Types | Features |
|---|---|
| Site-to-Site VPN | – Connects multiple offices securely – Enables resource sharing between locations |
| Remote Access VPN | – Allows employees to connect securely from remote locations – Access to company resources from anywhere |
| Extranet VPN | – Extends secure network access to trusted external entities – Facilitates secure collaboration with partners and clients |
| MPLS VPN | – Offers global connectivity with high performance – Utilizes MPLS technology for secure communication |
Choosing the right type of VPN for your business depends on your specific requirements and infrastructure. Secure VPN connections ensure privacy and protect sensitive data from potential threats. Additionally, VPN client software plays a crucial role in facilitating secure connections and simplifying the user experience. Implementing the appropriate VPN solution can enhance data security and streamline business operations.
VPNs for Streaming and Geo-restriction Bypassing
In today’s digital age, streaming services have become a popular way to access entertainment content. However, many streaming platforms enforce geo-restrictions, limiting access to certain content based on the user’s location. This can be frustrating, especially when your favorite shows or movies are unavailable in your country.
Fortunately, VPN services offer a solution to bypass these geo-restrictions and allow you to stream content from anywhere in the world. By encrypting your internet connection and routing it through servers located in different countries, VPNs can make it appear as if you are accessing the internet from a different location.
Best VPN Providers for Streaming
When it comes to finding the best VPN provider for streaming, there are several factors to consider. Speed and reliability are crucial, as you don’t want your streaming experience to be hindered by buffering or lag. Additionally, a wide server network and optimized streaming servers in different regions can ensure a seamless and uninterrupted streaming experience.
Here are some of the best VPN providers that excel at bypassing geo-restrictions and offer an exceptional streaming experience:
| VPN Provider | Server Network | Streaming Optimized Servers | Price |
|---|---|---|---|
| ExpressVPN | 3000+ servers in 94 countries | Yes | $6.67/month |
| NordVPN | 5500+ servers in 59 countries | Yes | $3.71/month |
| Surfshark | 1700+ servers in 63 countries | Yes | $2.49/month |
| CyberGhost | 7000+ servers in 91 countries | Yes | $2.25/month |
These VPN providers offer a wide range of server locations, ensuring that you can access content from around the globe. They also have specialized streaming-optimized servers that prioritize speed and performance for streaming services.
Keep in mind that the pricing may vary depending on the subscription length and promotional offers. Be sure to check their respective websites for the most up-to-date pricing information and additional features.
With a reliable VPN provider by your side, you can enhance your streaming experience and unlock a world of content that was previously inaccessible due to geo-restrictions.
Next, we will explore the use of VPNs for enhanced privacy and anonymity in Section 6.
VPNs for Enhanced Privacy and Anonymity
Privacy and anonymity are crucial when it comes to using a VPN. In this section, we will explore the different types of VPNs that prioritize privacy and discuss the technology that ensures your online activities remain anonymous.
VPN Types for Privacy
When it comes to VPNs, there are a few different types that are specifically designed to enhance your privacy. Let’s take a look at them:
- Logless VPNs: These VPN services do not keep any logs of your online activities. By not recording your browsing history or any other data, logless VPNs provide an added layer of privacy.
- Tor VPNs: Tor or The Onion Router is an anonymous network that routes your internet traffic through multiple servers, making it nearly impossible for anyone to trace your online activities back to you. Tor VPNs combine the anonymity of Tor with the security of a VPN, making them ideal for those who prioritize privacy.
- Double VPNs: Double VPNs add an extra layer of encryption by routing your internet traffic through two separate VPN servers. This double encryption process increases your anonymity and makes it extremely difficult for anyone to track your online activities.
It’s important to note that while these VPN types prioritize privacy, they may come with certain limitations. For example, Tor VPNs may be slower due to the multiple server hops, and double VPNs may require more bandwidth. However, if privacy is your top concern, these VPN types are worth considering.
VPN Technology for Anonymity
Behind the scenes, VPNs utilize various technologies to ensure your online activities remain anonymous. Here are some common technologies used:
- Encryption: VPNs use encryption algorithms to secure your internet connection and protect your data. This ensures that even if someone intercepts your data, they won’t be able to decipher or read it.
- IP Masking: VPNs mask your IP address, replacing it with the IP address of the VPN server you are connected to. This makes it virtually impossible for anyone to track your online activities back to your original IP address.
- Kill Switch: A kill switch is a feature that automatically disconnects your internet connection if the VPN connection drops. This prevents your online activities from being exposed to your ISP or other prying eyes.
By utilizing these technologies, VPNs ensure that your online activities remain private and anonymous.
| VPN Type | Description |
|---|---|
| Logless VPNs | These VPN services do not keep any logs of your online activities, providing an added layer of privacy. |
| Tor VPNs | Tor VPNs combine the anonymity of Tor with the security of a VPN, routing your internet traffic through multiple servers to make it nearly impossible to trace your activities back to you. |
| Double VPNs | Double VPNs encrypt your internet traffic and route it through two separate VPN servers, increasing your anonymity and making it extremely difficult for anyone to track your activities. |
VPNs for Enhanced Security on Public Wi-Fi
Public Wi-Fi networks can be a breeding ground for cyber threats. Hackers can easily intercept your data, compromising your sensitive information. This is where VPNs come to the rescue.
A secure VPN connection ensures that all your internet traffic is encrypted, providing an additional layer of security when connected to public Wi-Fi networks. By encrypting your data, VPN technology ensures that even if a hacker manages to intercept your information, they won’t be able to decipher it.
Using a VPN on public Wi-Fi is especially important when accessing sensitive information such as online banking portals or making purchases. With the ability to create a secure tunnel between your device and the VPN server, VPNs protect your personal details from falling into the wrong hands.
Here’s how VPNs enhance your security on public Wi-Fi:
- Data Encryption: VPNs use advanced encryption algorithms to scramble your data, making it unreadable to anyone trying to intercept it on public Wi-Fi networks.
- Secure Tunneling: VPNs create a secure tunnel through which your data is sent, preventing unauthorized access and ensuring that your information remains confidential.
- IP Address Masking: VPNs hide your IP address, making it difficult for snoopers on the same network to track your online activities.
- Protection from Malware: Some VPN services offer built-in malware protection, safeguarding your device from malicious software often found on public Wi-Fi networks.
To better understand the importance of secure VPN connections on public Wi-Fi, let’s take a look at a comparison of real-world scenarios:
| Scenario | No VPN | With VPN |
|---|---|---|
| Using online banking | Exposed to potential hackers | Encrypted connection ensures secure banking transactions |
| Accessing work emails | Data vulnerable to interception | Secure tunnel protects sensitive work-related communications |
| Online shopping | Risk of credit card information theft | Encrypted connection safeguards personal and financial data |
As illustrated in the table, using a VPN significantly enhances your security on public Wi-Fi networks. The secure VPN connections provided by VPN technology ensure your online activities remain private and your sensitive information stays protected from cyber threats.
Conclusion
In this article, we have explored the different types of VPN available and when to use them. We have discussed VPN services and compared popular VPN options to help you make an informed choice. Additionally, we have emphasized the importance of secure VPN connections in protecting your online activities.
Whether you need a VPN for personal use, business purposes, streaming, enhanced privacy, or security on public Wi-Fi, it is essential to select the right VPN based on your specific requirements. Consider factors such as speed, encryption protocols, server locations, and customer support when choosing a VPN service.
Remember, a premium VPN service like NordVPN offers a comprehensive range of features and excellent security measures. By utilizing a VPN, you can ensure your online privacy, bypass geo-restrictions, protect sensitive information on public networks, and maintain anonymity while browsing the internet.
FAQ
What are the different types of VPN?
The different types of VPN include remote access VPNs, site-to-site VPNs, and mobile VPNs. Remote access VPNs allow individuals to securely connect to a private network from a remote location. Site-to-site VPNs connect multiple networks, such as branch offices, over the internet. Mobile VPNs provide secure connectivity for mobile devices, ensuring data protection while on the move.
When should I use a VPN?
You should use a VPN when you want to secure your internet connection, protect your sensitive data, access geo-restricted content or bypass censorship, ensure privacy and anonymity online, or enhance security when using public Wi-Fi networks.
How does a VPN work?
A VPN works by creating a secure and encrypted connection between your device and the VPN server. When you connect to a VPN, all of your internet traffic is routed through this encrypted tunnel, preventing anyone from intercepting or monitoring your data. This ensures privacy and security while browsing the internet.
What technology is used in VPNs?
VPNs use various technologies to establish secure connections. These include tunneling protocols, encryption algorithms, and authentication methods. Common technologies used in VPNs include IPsec, OpenVPN, L2TP/IPsec, SSTP, and PPTP. Each technology has its own strengths and can be selected based on specific use cases and compatibility requirements.
Which VPN services are popular and reliable?
Some popular and reliable VPN services include ExpressVPN, NordVPN, CyberGhost, Surfshark, and Private Internet Access. These providers offer robust security features, fast connection speeds, a wide server network, and user-friendly interfaces. It is recommended to compare their features and pricing to choose the best one for your needs.
How can a VPN enhance security on public Wi-Fi networks?
When connected to a public Wi-Fi network, your data is vulnerable to interception by hackers. By using a VPN, you can encrypt your internet traffic, preventing unauthorized access to your sensitive information. This ensures that even if someone is monitoring the public Wi-Fi network, they will not be able to see your online activities or steal your data.
Are all VPN connections secure?
While VPNs provide encryption and privacy, not all VPN connections are equally secure. It is important to choose a VPN service that uses strong encryption algorithms, has a strict no-logs policy, and offers secure VPN protocols. Additionally, make sure to keep your VPN client software up to date to benefit from the latest security enhancements.
Can I use a VPN for streaming and bypassing geo-restrictions?
Yes, VPNs can be used to bypass geo-restrictions and access streaming content that is only available in certain regions. By connecting to a VPN server in a specific country, you can appear as if you are browsing from that location, granting you access to regionally restricted content.
Are there free VPN options available?
Yes, there are free VPN options available, but it is important to exercise caution when using them. Free VPNs may have limited server options, slower connection speeds, and may engage in practices that compromise your privacy, such as collecting and selling your data. It is recommended to thoroughly research and choose a reputable VPN service to ensure your privacy and security.
